At the end of 2024, I heard some news about an incoming wave of cheap and compact IP-KVM devices to control your computers or any other hardware that outputs video over HDMI and accepts input over USB.
Basically an alternative to integrated KVM-over-IP remote control hardware and software solutions: iLO (HP), iDRAC (Dell), or IPMI (SuperMicro). The problem is that these devices are typically embedded into large, expensive servers. And external commercial options are often very expensive, slow, and bulky. They also in many cases require proprietary browser plug-ins or applets to be installed.

If you're familiar with this concept and are aware of the key differences between a hardware IP-KVM and software remote desktop solutions like VNC, TeamViewer and others, you might also be on the lookout for a low-cost device like this.
PiKVM To The Rescue
No wonder that such projects as PiKVM are a godsend for those of us who have server(s) at home running 24/7, and would like to access and control said machines remotely in cases where the server has crashed and doesn't boot, or needs to be hard-reset by "holding a button", or anything in between. PiKVM was originally created as a pet project to develop a DIY KVM over IP. A lot has changed since then!
Nowadays you can either buy a ready-made PiKVM device…

…or still follow the DIY way and build one of your own (more on that below).

PiKVM were among the first ones to offer a complete open-sourced similarly named software solution and a DIY guide on how to build your own affordable KVM over IP device that utilizes a modern, secure, linux-based software stack.
But now there are new kids on the block! Are they any good?
Smaller, Cheaper, Chinese
It was only a matter of time before Chinese companies noticed a growing consumer and prosumer interest in such devices. So when I found out about a tiny low-power RISC-V KVM over IP device called "NanoKVM", and the fact that it was $20-30, I was immediately intrigued by the form-factor and the price of this product.

Knowing of the "Chinese" nature of the device and given an unfortunate fact that the company behind NanoKVM woudn't (or couldn't) make the device compatible with PiKVM open-source software, I did of course expect the software side of things to be inferior. I do have extensive experience with numerous Chinese devices and their drivers or bundled apps. And in vast majority of cases the software was terrible.
But I definitely did NOT expect this...
Insecure And… Shady?
It's a pretty technical deep dive into the security and overall software side of NanoKVM. You don't need to watch the whole video, just take note of the following key takeaways (referenced from the video description):
From GitHub repo of the part of the software that is actually open-sourced:
- NanoKVM is a Router (sysctl enables forwarding)
- SSH enabled with root:root (this will be changed after you login and set a new password, but it's still exposed even on the latest firmware image)
- NanoKVM bundles an outdated (and Sipeed-hosted) version of Tailscail
- NanoKVM presents as an InternetGatewayDevice, but isn't
- Setup fails on networks with China geo-blocked
- NanoKVM does not support MFA (really this is the least of your problems)
- tcpdump and aircrack are installed (aircrack is extremely useful for nefarious wifi things, and not useful on a kvm)
- DNS servers (re)set on every boot (even if you fix 8.8.8.8, it still reverts it 'for' you)
NanoKVM team did respond to some of this criticism here. Their original reply felt incomplete and dismissive. But seems like they've come up with a roadmap to try and fix all of the above. Call me when they do.
Discoveries of the author of the video, especially on the behavior of a closed-sourced library that the device makes use of:
- Default password (admin/admin) is poor, but also not forced to be changed. Same with SSH account (root/root). It will now prompt you to change, but this is not enforced.
- Passwords protected with absolutely raw-dogged AES and a 'secret' key which is just a string hardcoded into the Typescript
- No CSRF protection at all
- Auth token has long life instead of refresh
- User sessions cannot be invalidated
- Downloads .so from Sipeed after sending the devices serial number
- Downloads .so (and updates) do not check integrity, relying entirely on TLS
- Device uses custom DNS servers and you can't change it

Doesn't. Look. Good.
…And begs the question: why not simply use PiKVM's software stack to control the device? It is open-sourced after all.
Can NanoKVM Pro Do Better?

Nov, 2025 update: Seems like some of the newer models are actually compatible with PiKVM. Check out NanoKVM Pro documentation to find out how to set this up. Here's the product page as well — the Pro version starts at $79 for the base model, reaching $105 for one equipped with WiFi and PoE options. Plus either/and tax and PayPal fees.
According to the GitHub Pro-model promo section, the new device has a plethora of improvements, notably — a dual-core ARM CPU (which should be able to run circles around the RISC-V ones, used in the cheaper models), 4K/60 support, much lower latency, even lower than that of PiKVM, 1GBit/s LAN, a whole 1GB of LPDDR4X RAM and 32G of fast eMMC storage built-in. Looks very promising, especially now that PiKVM can be used with it instead of some other lesser-known bespoke software. This, naturally, doesn't guarantee that there aren't or wouldn't be any hardware backdoors or similar surprises, but at least there's that.
What's even cooler is that PiKVM compatibility means this thing can run Linux. Which, coupled with quite a bit of ROM and RAM means you can even make it host some other services on the network, run Python scripts, act as an SSH jump gate and anything else your typical low-power/cheap Linux VPS can be used for.
I'm certainly intrigued.
PiKVM VS The Chinese IP-KVM Debacle
One of the main reasons NanoKVM (and some other products) are having difficulties supporting the PiKVM software is somewhat unexpected: PiKVM devs don't want some of these companies to make PiKVM-compatible hardware and/or bundle PiKVM software with the existing ones.
Here's a video by Jeff Geerling reviewing yet another IP-KVM device – JetKVM:
What we're interested in are the comments below the video that shed some light on this topic:
Hey just wanted to let you know that PiKVM has been aggressively removing any mention of downstream devices from their communities. Someone even had their post on reddit removed just for asking if they could run it on their Pi zero. I would reconsider calling them the gold standard with their behavior.
Or:
They're removing even things about people experimenting with their own DIY stuff, someone simply asking if they could run it on a pi zero. Also It's tough because I'm someone who donates a considerable chunk of money towards open source I rely on, but that doesn't matter when I post "hey here's how to upgrade a BliKVM" and I have no community to post it in because it gets removed. The problems surrounding supporting open projects still exist regardless of the way I handle supporting projects I use.
Personally, I don't blame the PiKVM team for reacting this way. See, it's all because of how the other manufacturers are making use of the PiKVM software.
Jeff summarized this pretty well in one of his replies:
However, as a number of Chinese manufacturers started building their devices with PiKVM software but without contributing anything back, that started to turn the community a bit sour sometimes, because of the 'maker/taker' problem inherent to OSS. TinyPilot also fought a bit in that battle, as they were contributing back stuff, but were also burned—sometimes even with their code being ripped off with all the license headers removed!
So if PiKVM don't want their software being used like that, they're free to act however they like. I just hope they don't break compatibility with the existing PiKVM kits, including those people built on their own.
A DIY PiKVM?
Yes!
You can build your own PiKVM (as the whole software side of the project is still open-sourced). As a matter of fact, I know that this is possible precisely because I built one of my own back in 2021.
At first, it looked like this:

And after a bit of customization ended up as a pretty cool-looking (and robust) DIY IP-KVM device based on Raspberry Pi4:

The finished KVM comes in handy from time to time when I need to reinstall an OS on a device with no display, or in other more niche cases where software remote desktop solutions are not feasible. I didn't end up hooking it up to my home server permanently simply because most of the time I'm located close to the server and can perform maintenance directly. But if I were to leave for several weeks, I would absolutely utilize PiKVM to be able to have "physical" control over the server.
On a software side there's nothing to complain about. PiKVM is an excellent set of tools to control your PiKVM. It's fast, secure and regularly gets updates with new features.
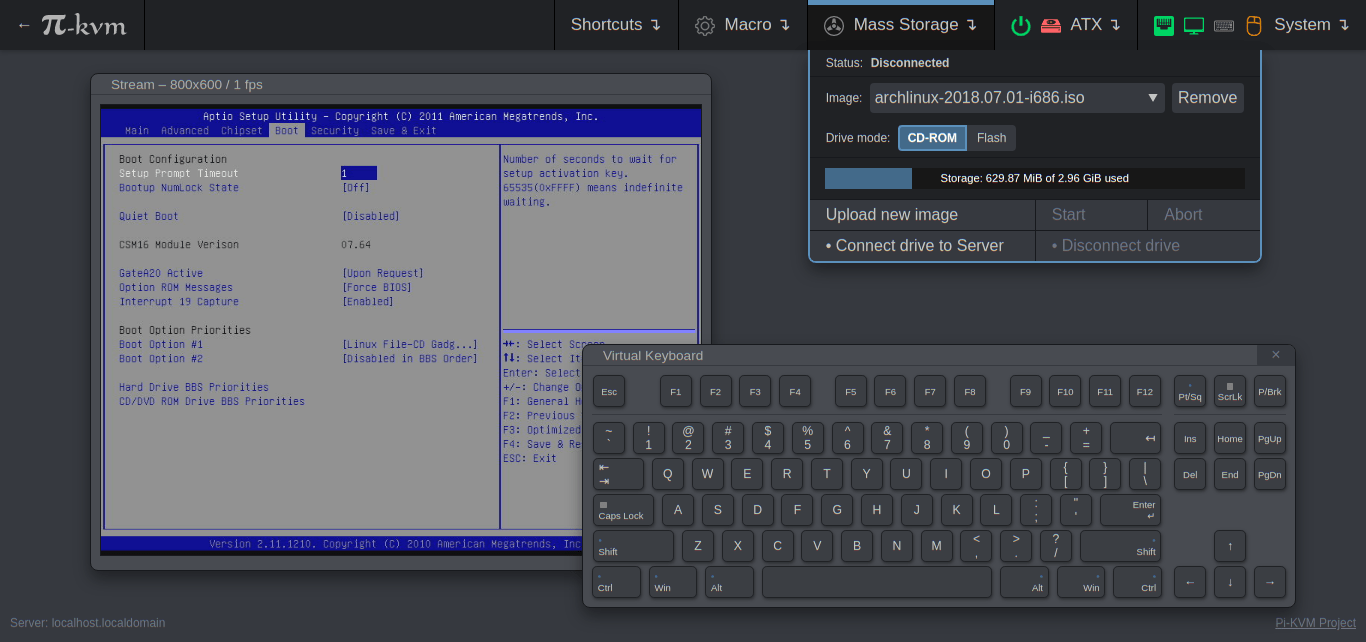
Therefore I would recommend either building your own PiKVM-compatible device using Raspberry Pi4 or Pi5 with an HDMI capture module, or purchasing one from the PiKVM team. The latter being a pricier, but complete option. Sure, these guys had been acting pretty aggressive towards other hardware manufacturers who wish to use their PiKVM software as base, but the stack itself is still FOSS, and they never removed the guides on how one could build their own PiKVM device. This shows that's it's not (at least not yet) done as an attempt to force you into buying an IP-KVM only from them.
PiKVM unit, regardless of whether you build one or buy one, will cost more than a Chinese IP-KVM like NanoKVM. In this particular case – one that comes with with some very sketchy closed-source binaries which are directly downloaded over the internet without any verification. And then executed in place. Code, which regularly phones home and utilizes undocumented (!) CPU opcodes to perform some shady activities in the background.
All of that — on your local network without your consent or knowledge.
It's up to you to decide which approach and/or product fits your goals and budget. But at least now you'll be a bit more informed on the potential security risks that arise with a typical cheap Chinese KVM over IP device.
Stay safe!
